The digital landscape is a relentless battlefield, a complex web where innovation clashes daily with sophisticated threats. Every minute, new vulnerabilities emerge, and malicious actors sharpen their tools, ready to exploit any weakness. In this high-stakes environment, merely reacting to attacks is a losing strategy. Instead, proactive defense is paramount, and that's precisely where understanding and applying robust Ethical Hacking Techniques & Methodologies becomes indispensable for system resilience.
Ethical hacking isn't about breaking the law; it's about anticipating the enemy's moves, understanding their tactics, and shoring up defenses before a breach occurs. Think of it as hiring a professional safe-cracker to test your vault, not to steal its contents, but to identify how it could be compromised so you can reinforce it. This guide cuts through the jargon to offer a clear, actionable roadmap to understanding these crucial techniques, helping you build a truly resilient digital infrastructure.
At a Glance: Your Quick Guide to Ethical Hacking
- What it is: The authorized practice of simulating cyberattacks to find and fix system vulnerabilities proactively.
- Why it matters: Prevents data breaches, reduces financial losses, builds customer trust, and ensures compliance.
- The Players: White hats (ethical hackers), black hats (malicious), and grey hats (operate in a grey area).
- The Process: A structured, multi-phase methodology from information gathering to detailed reporting.
- Key Benefit: Transforms your security posture from reactive firefighting to proactive fortification.
- Growing Need: The demand for skilled ethical hackers has skyrocketed, with a 65% global workforce growth needed and 33% projected growth in the next decade for the role.
The Digital Battleground: Why Ethical Hacking Isn't Optional Anymore
Cybercrime isn't just an abstract threat; it's a rapidly escalating crisis impacting organizations of all sizes. During the COVID-19 pandemic alone, global cybercrime surged by an alarming 600 percent. Every organization, from a local startup to a multinational corporation, sits squarely in the crosshairs of these sophisticated digital assaults. The question isn't if you'll face a cyberattack, but when—and whether you'll be prepared.
This preparation is the core mission of ethical hacking. It's a specialized discipline where cybersecurity professionals, often called "white hat hackers," use the same tools and techniques as malicious attackers but with one critical difference: explicit permission. Their goal is not to cause harm but to identify weaknesses, expose vulnerabilities, and provide actionable intelligence to strengthen an organization's defenses, ensuring its system resilience.
Understanding the Hacker Spectrum: White, Black, and Grey Hats
To truly grasp ethical hacking, it helps to understand the diverse landscape of those who wield hacking skills:
- White Hat Hackers (Ethical Hackers): These are the cybersecurity heroes. Employed legally by organizations, they use their profound knowledge of systems and networks to find and fix vulnerabilities. Their work is sanctioned, transparent, and always aimed at improving security. They are the proactive defenders, the ones who help ensure your digital assets are protected against the dark forces.
- Black Hat Hackers (Malicious Hackers): These are the cybercriminals. Operating illegally, they exploit vulnerabilities for personal gain, aiming to steal data, disrupt services, hold systems for ransom, or simply cause chaos. Their actions inflict significant financial losses and reputational damage on victims.
- Grey Hat Hackers: These individuals operate in a fascinating, often controversial, middle ground. They might exploit a vulnerability without authorization, much like a black hat, but typically without malicious intent. Their motivation is often to expose a flaw to the affected organization, sometimes seeking a "bug bounty" or simply recognition. While their intentions might be good, their unauthorized access can still carry legal risks.
The Soaring Demand for Cyber Defenders
The sheer volume and sophistication of cyber threats have created an unprecedented demand for skilled ethical hackers. A 2021 study highlighted the need for the global cybersecurity workforce to grow by a staggering 65 percent to adequately address current and future challenges. Looking ahead, the U.S. Bureau of Labor Statistics projects a robust 33 percent growth for ethical hacking-related roles in the next decade. These experts are critically needed across every sector imaginable—finance, healthcare, government, and technology—where the integrity and confidentiality of data are paramount.
The Unseen Shield: Core Benefits of Proactive Security
Engaging in ethical hacking isn't just a technical exercise; it's a strategic investment in an organization's future. The benefits extend far beyond simply patching a hole.
- Identifying Vulnerabilities Before Exploitation: This is the cornerstone. Ethical hackers proactively uncover flaws in systems, applications, and networks—from outdated software to misconfigured firewalls—before malicious actors can exploit them. It's about finding the cracks in your armor before the battle begins.
- Preventing Costly Data Breaches: By rectifying security flaws, organizations can protect sensitive information, customer data, and intellectual property. A single data breach can cost millions in direct damages, legal fees, regulatory fines, and lost business. Proactive measures are significantly less costly than recovering from an attack.
- Improving Security Awareness: Ethical hacking exercises often reveal common human vulnerabilities, such as susceptibility to phishing attacks. The insights gained help organizations educate employees on best practices, fostering a more security-conscious culture.
- Ensuring Compliance with Regulations: Many industries are bound by stringent data protection and privacy regulations (e.g., GDPR, HIPAA, PCI DSS). Regular ethical hacking assessments help organizations demonstrate due diligence and meet these critical compliance requirements, avoiding hefty penalties.
- Minimizing Financial Losses: Proactive vulnerability management is an investment that pays dividends. The cost of a penetration test or a vulnerability assessment is a fraction of the potential financial losses, legal liabilities, and reputational damage resulting from a successful cyberattack.
- Protecting Customer Trust and Reputation: In an era where data privacy is paramount, customers expect their information to be secure. Demonstrating a commitment to robust cybersecurity, often by showcasing regular ethical assessments, helps build and maintain invaluable customer trust and a strong brand reputation.
- Staying Ahead of Evolving Cyber Threats: The threat landscape is dynamic. What's secure today might be vulnerable tomorrow. Ethical hacking provides a continuous loop of testing and updating security measures, ensuring an organization's defenses evolve as rapidly as the threats themselves.
- Strengthening Network and Application Security: Beyond finding individual flaws, ethical hacking methodologies provide a holistic view of an organization's security posture. This leads to stronger network architecture, more secure application development practices, and resilient critical infrastructure. For organizations seeking a robust, future-proof security approach, a deep dive into a Code White comprehensive guide offers invaluable strategies for foundational resilience.
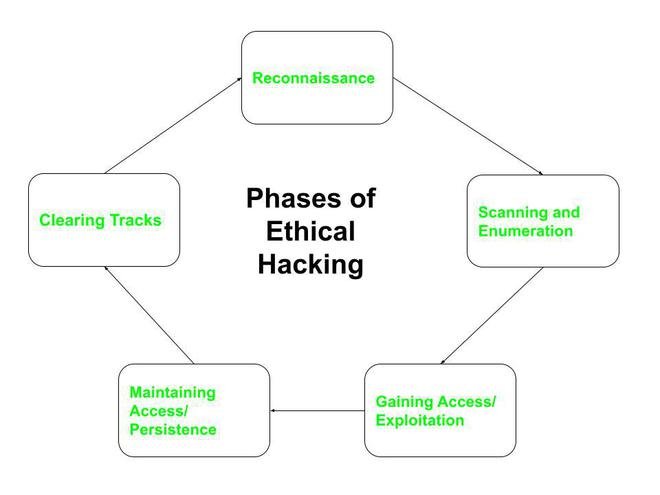
Blueprint for Resilience: The Ethical Hacking Methodology, Step-by-Step
Ethical hacking isn't a random probing mission. It follows a highly structured, systematic methodology, mimicking the phases a malicious attacker would undertake. This structured approach ensures thoroughness, replicability, and comprehensive coverage of potential attack vectors.
Phase 1: Reconnaissance – The Art of Silent Observation
This initial phase is all about gathering as much information as possible about the target system or network without directly interacting with it in a way that would trigger alerts. Think of it as a detective quietly observing a suspect from a distance before making any moves.
- Passive Reconnaissance: This involves collecting publicly available information. It's like sifting through open-source intelligence (OSINT).
- Examples: Using search engines like Google to find company websites, employee LinkedIn profiles, press releases, or leaked documents. Checking Wikipedia for organizational history. Utilizing
who.isto find domain registration details. Tools likesublist3rcan find subdomains associated with a target, whilewappalyzercan identify web technologies used by a site (e.g., WordPress, Nginx, specific JavaScript libraries). This treasure trove of data helps build a comprehensive profile of the target. - Active Reconnaissance: This involves direct interaction with the target system, which carries a higher risk of detection but yields more specific information.
- Examples: Pinging IP addresses to see if a host is alive, port scanning (though more detailed port scanning comes in Phase 2), or even making phone calls to employees under pretext to gather organizational details. The goal is still to gather information, but with a more direct, albeit cautious, approach.
Phase 2: Scanning & Enumeration – Mapping the Digital Terrain
Once initial information is gathered, ethical hackers begin actively probing the network to gain a more detailed understanding of its structure, active devices, open ports, and potential vulnerabilities. This is where the map of the digital terrain begins to take shape.
- Network Scanning: This process involves identifying active hosts on a network, determining their operating systems, and discovering open ports and running services.
- Tools:
Nmap(Network Mapper) is the undisputed king here. It can perform various scans to identify what services are listening on which ports (e.g., HTTP on port 80, SSH on port 22, SMB on port 445). Understanding open ports is crucial because each open port represents a potential entry point. - Vulnerability Scanning: This automated process uses specialized tools to identify known security weaknesses in systems and applications. These scanners compare system configurations and software versions against databases of known vulnerabilities.
- Examples: Common findings include outdated software, missing security patches, weak configurations, or default credentials. While powerful, these scanners primarily identify known vulnerabilities; they don't typically find zero-day exploits.
- Enumeration: This step is about extracting highly detailed information about network resources, shares, user accounts, and applications. It dives deeper than scanning, trying to identify specific instances and configurations.
- Tools:
Nmapcan also be used for enumeration scripts.Dirbusterhelps find hidden directories and files on web servers.Metasploitcan assist with enumerating system details once a foothold is established.ExploitDBandBurp Suite(for web applications) are invaluable for understanding existing exploits and potential attack vectors.Enum4linuxfocuses on Windows/Samba enumeration, detailing user lists, group memberships, and share information. The depth of insight gained here is often directly proportional to the likelihood of successful exploitation in the next phase, highlighting why comprehensive methodologies are so important for a robust cybersecurity framework.
Phase 3: Gaining Access – Exploiting the Weak Points
This is the phase where the rubber meets the road. Based on the vulnerabilities identified in the previous phases, ethical hackers attempt to exploit weaknesses to gain unauthorized access to the target system or network.
- Techniques:
- Brute Force Attacks: Trying countless combinations of usernames and passwords until the correct one is found.
- Dictionary Attacks: A more refined brute force, using lists of common passwords or words.
- Password Spraying: Attempting one common password against many accounts, rather than many passwords against one account, to avoid lockout policies.
- Phishing: Tricking users into revealing credentials or installing malware through deceptive emails or websites.
- Exploiting Software Vulnerabilities: Using known exploits for specific software versions or operating system flaws.
- Tools:
Metasploitis the premier framework for this phase. It provides a vast database of exploits, payloads, and modules to gain access to vulnerable systems. Its modular nature allows ethical hackers to select and customize attacks based on the target's identified weaknesses.
Phase 4: Privilege Escalation – Climbing to Command
Once initial access is gained, it's often with the privileges of a standard user. The goal of privilege escalation is to move from this limited account to a higher-level administrative control, such as Administrator or System on Windows, or root on Linux. This elevated access allows for deeper system control, data access, and the ability to modify critical configurations.
- Methods:
- Cracking Local Password Hashes: If an attacker gains access to a system, they might find password hashes stored locally. These can sometimes be cracked offline to reveal plaintext passwords.
- Exploiting Service Misconfigurations: Many services run with elevated privileges; if misconfigured, they can be exploited to gain the same level of control.
- Using Default or Reused Passwords: Shockingly common, default credentials or passwords reused across systems provide an easy path to higher privileges.
- Harvesting SSH Keys: Secure Shell (SSH) keys are used for secure remote access; if compromised, they can grant direct access.
- Utilizing
find,sudo, or SUID Binaries: On Linux, improperly configuredfindcommands, weaksudorules, or vulnerable SUID (Set User ID) binaries can be exploited to run commands with elevated privileges. This phase is critical for truly assessing the depth of a potential breach, and a comprehensive Code White analysis would meticulously document such findings.
Phase 5: Maintaining Access – Setting Up Persistence
After achieving desired access levels, ethical hackers might install backdoors, rootkits, or other persistent mechanisms. This is done to ensure they can regain access to the compromised system even if initial entry points are closed, mimicking how a malicious attacker would seek to maintain a long-term presence. This phase aims to evaluate how difficult it would be for an attacker to remain undetected and retain control over time.
Phase 6: Covering Tracks – The Art of Vanishing (with a caveat)
In a real-world malicious attack, this phase involves deleting or altering system logs, removing forensic evidence, and generally trying to avoid detection. For ethical hackers conducting authorized penetration tests, this step is often not performed in practice, or it's carefully simulated and documented. The primary goal of an ethical hack is to identify vulnerabilities, not to erase the audit trail. If executed, it would be to demonstrate how an attacker could cover their tracks, providing insights into improving log monitoring and intrusion detection systems.
Phase 7: Reporting – Your Blueprint for Stronger Defenses
The final and arguably most crucial phase for an ethical hacker is comprehensive reporting. This isn't just a list of findings; it's a detailed, actionable blueprint for improving security.
- Key Components of a Report:
- Executive Summary: A high-level overview of the assessment, key findings, and overall risk posture for management.
- Detailed Findings: Each vulnerability discovered, its severity (e.g., Critical, High, Medium, Low), the methods used to discover it, and the potential impact if exploited.
- Proof of Concept: Evidence (screenshots, code snippets) demonstrating successful exploitation without causing harm.
- Recommended Remediation Steps: Clear, specific, and prioritized actions the organization should take to fix each vulnerability. This is where the ethical hacker provides immense value, transforming problems into solutions.
- Risk Analysis: An assessment of the likelihood and impact of each vulnerability, helping organizations prioritize remediation efforts. This phase directly influences an organization's ability to achieve long-term system resilience, a core focus of a Code White comprehensive security assessment.
Tools of the Trade: Essential Kits for Ethical Hackers
Ethical hackers rely on a robust toolkit, constantly updated to keep pace with new threats and technologies. Here's a glimpse into some indispensable tools:
- Nmap (Network Mapper): A free and open-source utility for network discovery and security auditing. It's used for host discovery, port scanning, OS detection, and service version detection.
- Metasploit Framework: The world's most used penetration testing framework. It provides a platform to develop, test, and execute exploits, offering a vast array of payloads and modules.
- Burp Suite: A leading web vulnerability scanner and proxy tool. It's essential for testing web applications for a range of issues, from SQL injection to cross-site scripting (XSS).
- Dirbuster / OWASP ZAP: Tools for discovering hidden files and directories on web servers, which can sometimes reveal sensitive information or configuration files. OWASP ZAP also offers comprehensive web vulnerability scanning.
- Enum4linux: A utility for enumerating information from Windows and Samba hosts, including user lists, group memberships, and share details.
- Sublist3r: A Python tool designed to enumerate subdomains of websites using OSINT.
- Wappalyzer: A browser extension and online tool that identifies web technologies used on websites.
- ExploitDB: A public archive of exploits and vulnerable software. Ethical hackers use it to research existing exploits for identified vulnerabilities.
For organizations looking to integrate these methodologies into a robust security program, platforms like eProtect360 offer comprehensive features designed to support ethical hacking efforts. This includes automated scanning capabilities for continuous monitoring, real-time alerts for emerging threats, detailed reporting that aligns with ethical hacking outcomes, user-friendly interfaces for managing vulnerability assessments, and robust integration capabilities with existing security infrastructure. Such platforms become invaluable allies in maintaining a strong and adaptable security posture.
Ethical Hacking vs. Penetration Testing: Clearing the Air
It's common to hear "ethical hacking" and "penetration testing" used interchangeably, but there's a subtle yet important distinction worth clarifying for anyone serious about improving their security posture.
- Ethical Hacking: This is a broader term encompassing the entire discipline of using hacking skills for defensive purposes. It includes vulnerability assessments, security audits, and penetration tests. An ethical hacker might perform a range of activities, from reviewing code to setting up honeypots, all with the goal of improving security.
- Penetration Testing (Pen Test): This is a specific type of ethical hacking engagement. A pen test is a highly focused, time-bound simulation of a real-world cyberattack. It aims to exploit identified vulnerabilities to demonstrate the potential impact of a successful breach. Pen tests typically follow the phases outlined above (reconnaissance to reporting) and often have a defined scope (e.g., testing a specific application or network segment).
In essence, all penetration testing is ethical hacking, but not all ethical hacking is penetration testing. Penetration testing is a crucial methodology within the broader discipline of ethical hacking, providing a snapshot of an organization's defenses against a simulated attack.
Building Your Cybersecurity Fort: Practical Takeaways and Next Steps
The world of cybersecurity is in constant flux, and the insights gleaned from understanding Ethical Hacking Techniques & Methodologies are more critical than ever. It's a continuous journey, not a destination.
- Embrace a Proactive Mindset: Don't wait for a breach to happen. Integrate regular ethical hacking assessments—from vulnerability scans to full-scale penetration tests—into your security lifecycle. This proactive stance is the most effective defense.
- Invest in Continuous Education: For individuals aspiring to become ethical hackers, continuous learning is non-negotiable. The landscape changes daily, requiring ongoing skill development, certification, and staying updated on the latest threats and tools.
- Prioritize Remediation: Discovering vulnerabilities is only half the battle. The true value of ethical hacking lies in the diligent and timely remediation of identified flaws. Prioritize fixes based on severity and potential impact.
- Foster a Culture of Security: Technical controls are vital, but human factors are often the weakest link. Use insights from ethical hacking (e.g., successful phishing simulations) to educate employees and build a strong security-aware culture across your organization.
- Leverage Comprehensive Platforms: Tools and platforms like eProtect360, which offer automated scanning, real-time monitoring, and detailed reporting, can significantly streamline and enhance your ethical hacking efforts, providing continuous oversight and actionable intelligence.
- Consider Expert Partnerships: For organizations lacking in-house expertise, partnering with specialized cybersecurity firms for ethical hacking services can provide invaluable insights and bolster defenses effectively.
By understanding and actively applying the principles and methodologies of ethical hacking, you're not just reacting to threats; you're building a formidable, resilient digital fortress, prepared to withstand the cyber challenges of today and tomorrow. The future of security belongs to those who think like an attacker but act with integrity and foresight.