The digital landscape is a minefield, and software vulnerabilities are often the biggest explosive devices. In an era where cyberattacks are relentless and regulatory bodies increasingly hold developers accountable, merely bolting on security at the end of the software development lifecycle (SDLC) is no longer a viable strategy. Instead, organizations must embrace Secure Software Development Practices, weaving security into the very fabric of every phase, from initial concept to deployment and beyond. This isn't just a best practice; it's an operational imperative that protects your customers, your business, and your reputation.
This comprehensive guide will arm you with the knowledge to build security in, not just layer it on.
At a Glance: What You'll Learn
- Why shifting security left is critical: Understanding the financial, reputational, and regulatory costs of neglecting early security integration.
- The pillars of a strong security policy: How to define guidelines for people, processes, and technology.
- Essential frameworks: Navigating NIST SSDF, OWASP Top Ten, and ISO 27001 to structure your efforts.
- Core design principles: Architecting software with security baked in from day one.
- Practical best practices: A checklist of actionable steps to implement throughout your SDLC.
- Moving forward: A roadmap for continuous improvement in your secure development journey.
The High Cost of Lagging Security: Why "Bolt-On" Is Broken
For too long, security has been treated as an afterthought—a quality assurance check performed just before launch, much like testing for bugs. This "bolt-on" approach is fundamentally flawed in today's threat landscape. Cybercriminals are relentlessly exploiting software vulnerabilities, turning applications into gateways for data breaches, system compromises, and financial ruin.
Consider the real-world implications:
- Financial Drain: The average cost of a data breach continues to climb, often running into millions of dollars, not including legal fees and regulatory fines.
- Reputational Damage: News of a security incident can erode customer trust overnight, leading to lost business and a tarnished brand that takes years to rebuild.
- Regulatory Scrutiny: Regulators like the Securities and Exchange Commission (SEC) and Federal Trade Commission (FTC) are increasingly holding organizations and their developers accountable for poor development practices that lead to vulnerabilities. Compliance with standards such as SOC 2 and ISO 27001 isn't just a badge of honor; it's often a business necessity, and these standards demand integrated security.
The simple truth is that finding and fixing a vulnerability after deployment is exponentially more expensive than catching it during the coding or unit testing phase. Think of it like a structural flaw in a building: it's far cheaper to correct it on the blueprint or during initial construction than to tear down and rebuild a completed skyscraper.
Shifting Left: Integrating Security Throughout the SDLC
The solution to the "bolt-on" problem is a methodology often called DevSecOps, or more broadly, the practice of integrating security into every phase of the Software Development Life Cycle (SDLC). This "shifting left" principle means security isn't a final gatekeeper but an active participant from inception.
To truly embed security from the get-go, your organization should focus on three critical actions:
1. Test Early and Often with Precision
Security testing should not be a one-time event. It needs to be a continuous process employing a variety of techniques:
- Static Application Security Testing (SAST): These tools (like SonarQube or Checkmarx) analyze your source code without executing it. They catch common coding errors, potential backdoors, and deviations from secure coding standards early in the development phase, often right in the developer's IDE.
- Dynamic Application Security Testing (DAST): DAST tools (such as OWASP ZAP) examine the running application, simulating attacks to find vulnerabilities that might only appear during execution. This provides real-time insights into how your application responds to malicious input or unexpected behavior.
- Interactive Application Security Testing (IAST): IAST combines elements of SAST and DAST, running within the application and monitoring its behavior, code execution, and data flow from the inside. This offers high accuracy and context-rich results.
- Software Composition Analysis (SCA): Given that modern applications rely heavily on open-source components, SCA tools scan your codebase for known vulnerabilities in third-party libraries and dependencies, helping you mitigate risks from external sources.
By integrating these testing methods into your CI/CD pipeline, you create a robust safety net that continuously evaluates your code's security posture.
2. Document Security Requirements Clearly
Just as you meticulously document functional requirements, security requirements deserve the same, if not greater, attention. During the planning phase, clearly define what "secure" means for your specific application. This isn't vague wishes; it's concrete, measurable criteria.
- Security Requirements Specification (SRS): Develop a comprehensive SRS that outlines how the software will protect data, authenticate users, handle errors securely, and defend against specific threat types.
- User Stories and Use Cases: Incorporate security considerations directly into user stories (e.g., "As a user, I want my password to be securely hashed so it cannot be easily compromised") and abuse cases (e.g., "An attacker attempts to inject malicious SQL queries to access sensitive data").
Clear documentation ensures that security isn't an option but a non-negotiable part of the design and implementation.
3. Conduct Risk Analysis During Design
Before a single line of code is written, analyze potential security risks. This proactive approach helps you design controls into the architecture rather than patching them later.
- Threat Modeling: Tools like the Microsoft Threat Modeling Tool help you systematically identify potential threats, vulnerabilities, and countermeasures. By breaking down the application's components, data flows, and trust boundaries, you can anticipate where attacks might occur and design defenses proactively.
- Attack Surface Analysis: Identify all points where an unauthenticated user could interact with the application. This includes APIs, input fields, and external interfaces, allowing you to prioritize hardening efforts.
Performing these analyses early helps you build resilience into the foundational design, making your software inherently more secure.
Building a Strong Foundation: The Secure Software Development Policy
A secure software development policy is your organization's blueprint for minimizing vulnerability risk across all phases of the SDLC. It's a formal set of guidelines that brings consistency and accountability, and for organizations adhering to standards like SOC 2 or ISO 27001, it's often a mandatory requirement.
This policy establishes clear rules for three critical areas:
People: Empowering a Security-Minded Culture
Your people are your first and strongest line of defense. A robust policy addresses:
- Defining Duties: Clearly outline security responsibilities for developers, QA engineers, project managers, and even business analysts. Everyone plays a role in security.
- Role-Specific Training: Provide continuous, role-specific security training. Developers need secure coding best practices; testers need to understand common vulnerabilities; architects need threat modeling expertise.
- Strict Employee Screening: Implement rigorous background checks and screening processes for all personnel involved in software development, especially those with access to sensitive code or systems.
- Segregation of Duties: Distribute critical tasks across different individuals or teams to prevent a single point of failure or malicious activity. For example, the person writing the code shouldn't be the only one approving its release to production.
Processes: Embedding Security into Workflows
Security should flow seamlessly within your operational procedures. Policy elements include:
- Separation of Environments: Maintain strict separation between development, testing, staging, and production environments. Data from production should be sanitized before being used in lower environments.
- Least-Privilege Access Control: Implement the principle of least privilege for all users and automated systems. Grant only the minimum access necessary for individuals or components to perform their required tasks, and no more.
- Version Control: Mandate the use of secure version control systems (e.g., Git) for all source code. This ensures traceability of changes, facilitates code reviews, and allows for quick rollbacks if vulnerabilities are introduced.
- Security Gates in CI/CD: Integrate automated security checks (SAST, DAST, SCA) as mandatory gates in your continuous integration and continuous deployment pipelines, halting builds that fail security criteria.
Technology: Securing Your Tools and Ecosystem
The tools and platforms you use are as critical as the code itself. Your policy should govern:
- Programming Language & Coding Hardening: Establish rules for approved programming languages, secure coding standards (e.g., input validation, secure error handling), and the use of approved libraries and frameworks.
- Secure Repositories: Mandate the use of secure, access-controlled code repositories for all intellectual property. Implement multi-factor authentication and encryption for these critical assets.
- Configuration Management: Define secure default configurations for all development tools, servers, and cloud resources, minimizing potential attack vectors from misconfigurations.
Navigating the Landscape: Key Security Frameworks
Aligning your practices with established secure software development frameworks provides structure, consistency, and a recognized benchmark for your security efforts. These frameworks distill years of expertise into actionable guidelines.
1. NIST Secure Software Development Framework (SSDF)
Developed by the National Institute of Standards and Technology, the SSDF offers a comprehensive, flexible framework mapping security practices across the entire development lifecycle to broader NIST cybersecurity guidelines. It's built around four core processes:
- Prepare the Organization (PO): This foundational phase ensures your team, processes, and technology are ready for secure software development.
- Tasks: Define organizational security requirements, provide role-specific training for developers and security personnel, select and integrate supporting security tools (SAST, DAST), and install security checks throughout the SDLC.
- Protect the Software (PS): Focuses on safeguarding all software components from tampering and unauthorized access throughout the development process.
- Tasks: Store all code, artifacts, and build components in secure, access-controlled repositories based on the least-privilege principle. Provide customers with integrity verification information (e.g., hashes, digital signatures) for software releases.
- Produce Well-secured Software (PW): This is the core of creating software with minimal vulnerabilities in its final releases.
- Tasks: Design and review software to align with defined security requirements, rigorously evaluate third-party components for known vulnerabilities, enforce secure coding best practices, configure the build process for security, and perform comprehensive code reviews, static/dynamic analysis, and penetration testing. It also covers configuring secure default settings and reusing trusted, verified components.
- Respond to Vulnerabilities (RV): Addresses how to identify and appropriately handle vulnerabilities in released software, and crucially, learn from them to prevent future occurrences.
- Tasks: Establish clear vulnerability reporting and response programs, expedite remediation efforts for discovered flaws, determine the root causes of vulnerabilities, and periodically update your SDLC with new security knowledge and lessons learned.
2. OWASP Top Ten
The Open Web Application Security Project (OWASP) Top Ten is a globally recognized list identifying the most critical security risks for web applications. It's not a complete framework, but an essential reference point that informs threat modeling, security testing, and developer training. Regularly reviewing this list (which updates periodically) helps organizations prioritize their security efforts against the most common and impactful attack vectors, such as Injection, Broken Authentication, and Cross-Site Scripting.
3. ISO/IEC 27001
While broader than software development, ISO/IEC 27001 provides international standards for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Achieving ISO 27001 certification demonstrates a commitment to robust information security, including secure software development practices, ensuring consistency, scalability, and traceability of all security measures.
Architecting Security: Core Design Principles
Building secure software isn't just about following rules; it's about thinking securely from the ground up. These design principles guide architects and developers in creating resilient applications:
- Security as Code: This principle involves embedding security features like input validation, robust encryption for data at rest and in transit, and secure storage mechanisms directly into the codebase. Security isn't externalized; it's part of the application's core functionality.
- Ensuring Secure Defaults: Applications should be configured with the strongest security settings enabled by default. This means SSL/TLS should be mandatory, unnecessary services should be disabled, and default passwords should never be used. Users should have to opt-out of security, not opt-in.
- Practicing Least Privilege: Every user, process, and component should have only the minimal set of permissions and access rights necessary to perform its legitimate function. This limits the blast radius if an account or component is compromised.
- Separation of Duties: Distribute critical tasks and responsibilities across different individuals or systems. No single person should have end-to-end control over a sensitive process, preventing fraud or error.
- Minimizing Attack Surface Area: Reduce the number of potential entry points an attacker could exploit. This involves removing unused features, disabling unnecessary services, closing unused ports, and simplifying code wherever possible. Less code, fewer features, means fewer places for vulnerabilities to hide.
- Complete Mediation: Every access request to a resource should be validated and authorized. This isn't just for initial access; it's for every subsequent access, ensuring that permissions aren't bypassed or inherited improperly.
- Failing Securely: When an application encounters an error or failure, it should do so in a way that does not compromise security. This means avoiding revealing sensitive data in error messages, logging failures securely without exposing secrets, and maintaining a secure state rather than crashing open.
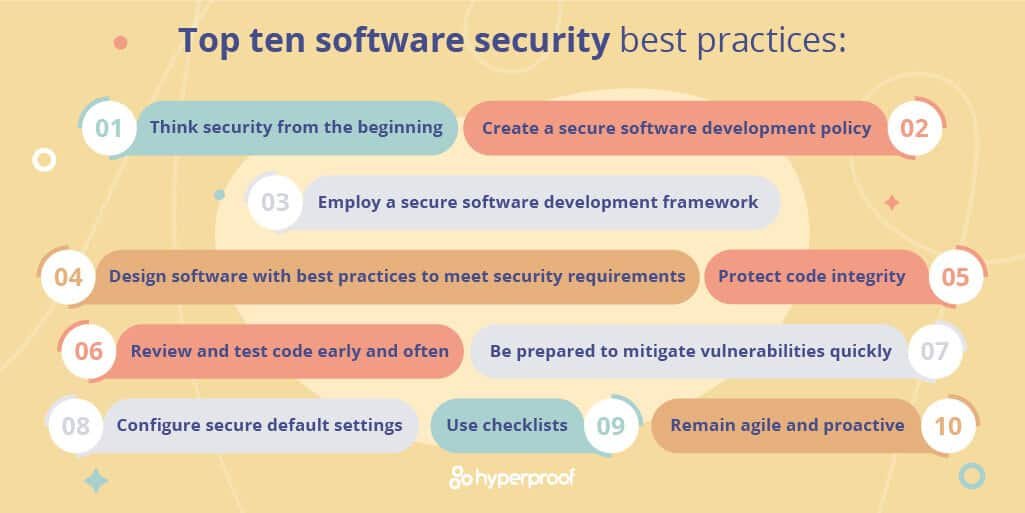
Your Action Plan: Top Secure Software Development Best Practices
Translating principles and frameworks into daily practice requires consistent effort and a clear roadmap. Here are the top secure software development best practices you should integrate:
1. Think Security from the Beginning
This cannot be stressed enough. Integrate security into the earliest phases: planning, requirements gathering, and design. Conduct threat modeling, define security requirements upfront, and establish secure coding standards before development begins. This proactive mindset is the cornerstone of DevSecOps.
2. Create a Comprehensive Secure Software Development Policy
Formalize your approach. Develop a clear policy that outlines guidelines for your people (training, roles, screening), processes (environment separation, access control, versioning), and technology (coding standards, secure repositories). This document is your internal constitution for security.
3. Employ a Secure Software Development Framework
Don't reinvent the wheel. Leverage established frameworks like the NIST SSDF to provide structure, consistency, and a proven methodology for your security initiatives. These frameworks offer a roadmap and ensure you're addressing a broad spectrum of risks. For deeper dives into these frameworks and more, you can explore resources like The Code White Hub.
4. Design Software with Best Practices to Meet Security Requirements
Move beyond just functional requirements. Actively design your software using principles like least privilege, secure defaults, and minimizing attack surface. Train your developers on these design paradigms and ensure that any third-party components or vendors also comply with your security standards.
5. Protect Code Integrity
Your source code is your intellectual property and a critical attack vector if compromised. Store code in secure, restricted repositories, implement strong version control, continuously monitor changes, and use code signing to verify the authenticity and integrity of your releases. This prevents unauthorized tampering and ensures code hasn't been maliciously altered.
6. Review and Test Code Early and Often
Embed rigorous reviews and testing throughout your SDLC. This includes peer code reviews, automated static application security testing (SAST) in development, dynamic analysis (DAST) in testing environments, and periodic manual penetration testing (ethical hacking) before production. Catching vulnerabilities early saves significant time and cost.
7. Be Prepared to Mitigate Vulnerabilities Quickly
No software is perfectly secure. Establish a dedicated vulnerability response team, a clear plan, and efficient processes for rapid detection, analysis, and remediation of any discovered vulnerabilities. Reducing the window of opportunity for exploitation is paramount. Implement robust patch management and incident response protocols.
8. Configure Secure Default Settings
By default, your applications, systems, and environments should be configured for maximum security. This means disabling unnecessary services, enforcing strong password policies, and enabling encryption without requiring user intervention. Make security the path of least resistance.
9. Use Checklists for Consistency
Implement security checklists at various stages of development. These can cover secure coding guidelines, deployment configurations, and pre-release security reviews. Periodically review and update these checklists to ensure your security policies and procedures remain current, effective, and consistently applied.
10. Remain Agile and Active: Continuous Improvement
The threat landscape is constantly evolving, so your security practices must evolve with it. Continuously study new vulnerabilities, analyze root causes of past incidents, identify patterns, and implement preventative measures. Stay updated on industry trends, emerging threats, and the latest secure development best practices. Security is not a destination; it's a continuous journey of learning and adaptation.
Your Roadmap to a More Secure Future
Embracing secure software development practices is a strategic investment, not merely a compliance burden. By integrating security early and often, fostering a security-conscious culture, and leveraging proven frameworks and best practices, you build more resilient software, protect your users, and safeguard your business.
Start by assessing your current SDLC. Where are the gaps in security integration? Which of these best practices can you realistically implement first? Even small, consistent steps towards "shifting left" can yield significant improvements in your security posture. This journey requires commitment, continuous learning, and a proactive mindset, but the rewards—in trust, stability, and reputation—are immeasurable. Your users deserve software that is not only functional but also inherently secure, and your business depends on it.