Vulnerability Assessment & Management: Finding and Fixing Security Gaps
Imagine your organization’s digital infrastructure as a grand, intricate building. You’ve invested heavily in its construction – strong walls, secure doors, advanced alarm systems. But what if a window was inadvertently left unlocked on the fifth floor? Or a contractor forgot to properly secure a back utility entrance? That single overlooked detail could compromise the entire structure. This is precisely the critical role of Vulnerability Assessment & Management in cybersecurity: it’s the continuous process of meticulously inspecting your digital "building" to find those unlocked windows and unsecured doors before a threat actor does.
It's not enough to build a secure system once; you need to constantly check it, maintain it, and patch it up. As technology evolves and threats grow more sophisticated, identifying and resolving security weaknesses becomes a foundational practice for any organization serious about protecting its assets and its reputation.
At a Glance: What You’ll Learn
- Vulnerability Assessments (VA) identify specific security flaws; Vulnerability Management (VM) is the ongoing, strategic program to handle them.
- Why it matters: Prevent data breaches, ensure compliance, enable faster fixes, and build stakeholder trust.
- The Lifecycle: A continuous five-step process from discovery to reporting.
- Types of Assessments: From networks to databases, covering every digital corner.
- Key Tools: Automated scanners, threat intelligence, and the indispensable human element.
- VA vs. Pen Testing: Understanding these distinct, yet complementary, security practices.
- Common Challenges: How to tackle overwhelming findings, false positives, and blind spots.
What is Vulnerability Assessment & Management, Anyway?
Let's break down the core concepts.
A vulnerability assessment (VA) is a systematic, point-in-time snapshot. Think of it as a detailed health check for your digital systems. It's the process of identifying, evaluating, and reporting specific security weaknesses – often called "vulnerabilities" – in your software, hardware, configurations, or operational processes. These weaknesses are the potential entry points that could be exploited by cyberthreats, leading to unauthorized access, data breaches, or system disruption.
Vulnerability management (VM), on the other hand, is the ongoing, strategic discipline that encompasses vulnerability assessments. It's a subdomain of IT risk management that involves continuously discovering, prioritizing, and resolving those identified security vulnerabilities. Where a VA is an event, VM is the entire lifecycle – a proactive, continuous commitment to reducing your organization's security risk posture over time.
This continuous approach is no longer optional. With the global average cost of a data breach reaching USD 4.44 million in 2023, leaving security gaps unchecked is a gamble few organizations can afford.
Why Bother? The Non-Negotiable Imperative of VA & VM
Ignoring potential weaknesses is like leaving your front door unlocked in a bustling city. The reasons to prioritize robust vulnerability assessment and management are clear and compelling:
- Managing Cyber Threats: Proactively identifying gaps before exploitation is your best defense against data breaches, the exposure of Personally Identifiable Information (PII), and devastating financial and reputational losses. It’s about being proactive, not reactive.
- Compliance with Regulations: Many industry standards and regulatory frameworks, such as PCI DSS (Payment Card Industry Data Security Standard) and NIST SP 800-53, explicitly mandate regular vulnerability scanning and meticulous documentation. Strong VM is not just good practice; it’s a legal and ethical requirement.
- Enabling Faster Remediation: A well-executed VA feeds prioritized vulnerabilities directly into your IT workflows. By integrating with patch management systems and operational teams, VM ensures that identified weaknesses are addressed swiftly and systematically, preventing minor issues from escalating into major incidents.
- Strengthening Stakeholder Trust: Demonstrating a clear, consistent commitment to protecting sensitive data, intellectual property, and operational continuity builds confidence among customers, partners, and investors. It’s a visible sign of a mature and responsible organization.
The Continuous Cycle of Security: The Vulnerability Management Lifecycle
Effective vulnerability management isn't a one-and-done task; it's a dynamic, iterative process. Think of it as a continuous loop of vigilance, repair, and improvement. This lifecycle typically involves five key phases:
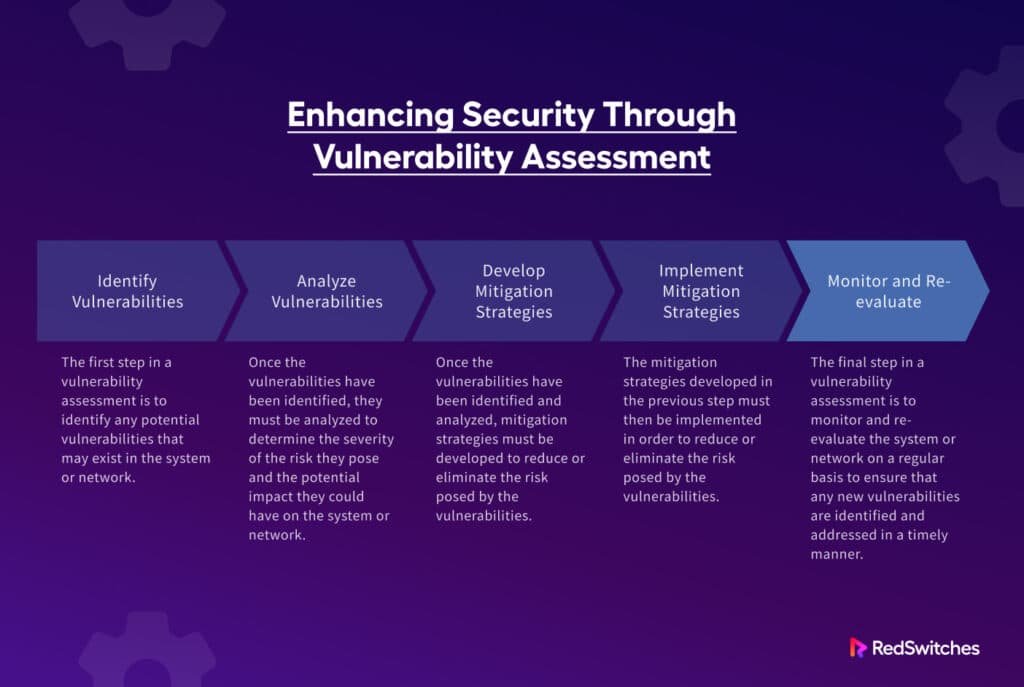
1. Discovery and Vulnerability Assessment
This is where you identify all your IT assets and actively hunt for weaknesses. It starts with knowing what you have: workstations, servers, network devices, cloud instances, mobile endpoints, applications, and more. Once your asset inventory is clear, you leverage automated tools and scanners to probe for known weak points. Tools like Nmap can help with host discovery and service enumeration, while specialized vulnerability scanners identify known vulnerabilities based on extensive databases of security flaws. For web applications, scanners like Nikto might check for common misconfigurations or vulnerabilities.
2. Vulnerability Analysis and Prioritization
Not all vulnerabilities are created equal. Discovering thousands of potential issues can be overwhelming. In this phase, you analyze identified vulnerabilities to understand their potential impact, relevance to your specific environment, and exploitability. This often involves cross-referencing findings with vulnerability databases (like CVE), open-source intelligence, and real-time threat intelligence feeds to determine which flaws are actively being exploited "in the wild." Prioritization ensures you tackle the most critical risks first, making efficient use of your resources. This is where a deep understanding of the essentials of threat intelligence becomes invaluable.
3. Vulnerability Resolution
Once prioritized, it’s time to act. Resolution isn't always about outright "fixing" a flaw. It comes in a few forms:
- Remediation: This is the ideal scenario – directly fixing the vulnerability. Common remediation steps include applying security patches, updating software versions, reconfiguring systems to align with security best practices, or correcting flawed code.
- Mitigation: If immediate remediation isn't possible (e.g., due to system criticality or lack of a patch), you might implement mitigating controls. This could involve deploying a firewall rule to block access to a vulnerable service, isolating a vulnerable system on a segregated network, or implementing an Intrusion Prevention System (IPS) to detect and block exploit attempts.
- Acceptance: For very low-risk vulnerabilities that have minimal impact and exploitability, and where remediation or mitigation costs outweigh the risk, an organization might formally accept the risk. This decision should always be documented, justified, and regularly reviewed.
4. Verification and Monitoring
After implementing fixes or mitigations, you can't just assume the problem is solved. This phase involves conducting re-testing or follow-up scans to confirm that the changes effectively resolved the vulnerability without introducing new issues. Continuous monitoring is also crucial to detect new vulnerabilities that emerge, identify any "configuration drift" (where systems revert to insecure states), and ensure that your security posture remains strong. This proactive approach helps maintain the integrity of your fixes.
5. Reporting and Improvement
The final phase closes the loop, but it also seeds the next iteration of the cycle. You'll document everything: the tools used, all identified vulnerabilities, the actions taken, the outcomes, and any remaining residual risk. Key metrics, such as Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR), are tracked to gauge the efficiency and effectiveness of your VM program. Dashboards are created to provide real-time visibility for stakeholders, enabling continuous improvement of your processes and demonstrating audit readiness. This iterative feedback loop is essential for refining your overall security strategy and often requires careful consideration of navigating cybersecurity risk frameworks.
Peeking Into Every Corner: Types of Vulnerability Assessments
Your digital "building" has many rooms, and each requires a different kind of inspection. Vulnerability assessments can be specialized to target specific parts of your infrastructure:
- Network-based Assessments: These scans target your internal and external network infrastructure. They look for open ports, insecure network protocols, misconfigured firewalls, and exposed network services that could serve as entry points for attackers. This is like checking the perimeter and main corridors of your building.
- Host-based Assessments: Diving deeper, these assessments focus on individual systems like servers, workstations, and operating systems. They detect software vulnerabilities, unauthorized applications, weak passwords, and misconfigurations at the operating system level. Think of this as inspecting each individual office or server room.
- Application Scans: Specifically designed for web applications, APIs, and other software applications. These assessments look for common vulnerabilities like SQL injection, cross-site scripting (XSS), broken authentication, insecure direct object references, and other OWASP Top 10 risks. This is inspecting the custom machinery and tools within each room.
- Wireless Network Assessments: These scans identify risks associated with your wireless networks. They might uncover rogue access points, weak encryption protocols (like WEP), or improper network segmentation that could allow unauthorized access. This is like checking the security of your building's Wi-Fi.
- Database Assessments: Focused on the heart of much organizational data, these assessments scan databases for security vulnerabilities. This includes checking for default credentials, poor access controls, outdated database engines, excessive user permissions, and unpatched security flaws. This is like inspecting the highly sensitive vault where your most valuable assets are stored.
Your Arsenal: Tools and Techniques for Effective Assessment
Effective vulnerability assessment combines automated tools for broad coverage, threat intelligence for context, and human analysis for critical thinking and validation.
The Core: Vulnerability Scanners
Vulnerability scanners are automated software tools that evaluate systems for known vulnerabilities. They work by comparing configuration settings, software versions, and network behaviors against vast, continuously updated databases of known security flaws (like those listed in the Common Vulnerabilities and Exposures - CVE list). They can identify everything from missing security patches to insecure default configurations.
Beyond Basic Scans: Specialized Tools
- Patch Management Tools: These systems automate the process of applying updates and security patches across your entire IT environment. They often integrate with asset discovery to prioritize which systems need patching most urgently, streamlining a critical part of the remediation process. Building an effective patch management program is essential.
- Application Testing Frameworks: For web and mobile applications, these tools go beyond simple vulnerability scanning. They simulate various attack types (e.g., SQL injection, XSS) and can help validate authentication mechanisms and session management, providing deeper insights into application-layer vulnerabilities.
- Threat Intelligence Platforms: These platforms provide crucial context by linking identified vulnerabilities with active exploits, current phishing campaigns, and known threat actor tactics. This helps prioritize vulnerabilities that are truly being targeted by real-world threats, making your remediation efforts far more strategic.
- Attack Surface Management (EASM) Tools: External Attack Surface Management tools offer continuous visibility into all internet-facing assets owned by an organization. They're invaluable for uncovering "shadow IT" or unnoticed access points that could become blind spots in traditional vulnerability scans.
- Open Source Utilities: Tools like Nmap for network discovery, Nikto for web server scanning, and various other open-source security tools provide immense flexibility for specialized scans and deeper, more manual analysis. While they may require more manual effort and expertise, they offer granular control and can uncover issues commercial scanners might miss.
The Indispensable Element: Human Expertise
While automated tools are powerful, they are not a silver bullet. Human analysts bring critical thinking, experience, and context that machines cannot replicate. They validate findings (reducing false positives), interpret complex results, and understand the unique business context of vulnerabilities, offering strategic guidance for remediation. Without human oversight, automated reports can quickly lead to alert fatigue and misdirected efforts.
Vulnerability Assessment vs. Penetration Testing: What's the Difference?
These two terms are often confused, but they serve distinct, though complementary, purposes in cybersecurity. Think of it this way:
- Vulnerability Assessments (VA): These are like a thorough home inspection. They aim to identify all potential weaknesses in your security posture, providing a broad overview of known risks. A VA catalogs existing security gaps and quantifies their severity. It answers the question, "What vulnerabilities do we have?" VAs are typically continuous or routine, providing an ongoing view of your security risks.
- Penetration Testing (Pen Testing): This is like hiring a skilled burglar to try and break into your home using the weaknesses the inspector might have found (or new ones). Pen testing is a targeted exercise where security experts (ethical hackers) actively attempt to exploit identified vulnerabilities to see how far they can get into your systems. It evaluates the effectiveness of your security controls and processes against a simulated real-world attack. Pen tests are typically scheduled at key intervals – for example, before a major product launch or after significant infrastructure changes. It answers the question, "Can someone actually exploit these vulnerabilities, and what damage could they do?"
Both are crucial. VA tells you what the problems are; pen testing shows you what could happen if those problems aren't fixed. A robust vulnerability management program often feeds critical findings into targeted penetration tests to validate remediation efforts and discover new attack paths.
Navigating the Minefield: Common Challenges and How to Overcome Them
Even with the best intentions and tools, organizations often stumble with vulnerability assessment and management. Here are some common pitfalls and practical ways to avoid them:
1. High Volume of Findings & Alert Fatigue
Large, complex environments can generate thousands of vulnerability findings. Without clear prioritization, security teams quickly become overwhelmed, leading to "alert fatigue" where critical alerts get lost in the noise.
- Solution: Implement robust prioritization frameworks. Focus on factors like exploitability (is there an active exploit in the wild?), impact (what data or systems are affected?), and asset criticality (how important is the vulnerable system to your business?). Leverage threat intelligence platforms to highlight actively exploited vulnerabilities.
- Solution: Integrate with business context. Understanding which vulnerabilities affect critical business processes or high-value data can dramatically narrow your focus.
2. False Positives
Automated scanning tools aren't perfect; they can sometimes flag non-issues or misinterpret configurations as vulnerabilities. Chasing down false positives wastes valuable time and erodes trust in the scanning process.
- Solution: Validate findings with human analysis. Security analysts should review and confirm suspicious alerts before escalating them for remediation.
- Solution: Tune your scanners. Configure tools to specific environments, exclude irrelevant checks, and whitelist known secure configurations to reduce noise over time.
3. Blind Spots and Limited Visibility
"Shadow IT" (unmanaged devices or applications), overlooked cloud instances, or third-party applications can create significant gaps in your vulnerability assessments, leaving ideal targets for threat actors. If you don't know it exists, you can't scan it.
- Solution: Implement robust asset discovery. Use EASM tools for external visibility and integrate with internal asset management systems to maintain a comprehensive, up-to-date inventory of all IT assets.
- Solution: Develop clear policies for asset onboarding and offboarding. Ensure all new systems and applications are brought under security scrutiny from day one.
4. Operational Disconnects
Often, security teams identify vulnerabilities, but IT operations teams are responsible for remediation. Siloed teams, poor communication, or conflicting priorities can delay crucial remediation efforts.
- Solution: Foster cross-functional collaboration. Establish clear communication channels, shared metrics, and joint ownership of remediation goals. Integrate vulnerability management platforms with IT service management (ITSM) tools to automate ticket creation and tracking.
- Solution: Implement a security champions program. Designate individuals within IT operations to be security advocates, bridging the gap between security requirements and operational realities. This collaborative spirit is also vital when it comes to creating a robust incident response plan.
Building a Robust Program: Best Practices for Success
Moving beyond just understanding what Vulnerability Assessment & Management entails, here's how to build a truly effective program that stands the test of time and evolving threats:
- Integrate Early, Automate Smart: Don't treat security as an afterthought. Build security into your development and deployment pipelines (DevSecOps). Automate vulnerability scanning as part of your CI/CD process. Automate patch deployment for non-critical systems. The more you automate routine tasks, the more human analysts can focus on complex analysis and strategic initiatives.
- Prioritize Ruthlessly: You can't fix everything at once. Develop a clear, objective prioritization matrix that considers the Common Vulnerability Scoring System (CVSS), exploitability in the wild (via threat intelligence), and the business criticality of the affected asset. Focus on high-risk, high-impact vulnerabilities first. This focused approach is key to Understanding Code White – a concept where proactive security measures prevent critical vulnerabilities before they impact systems.
- Establish a Regular Rhythm: Vulnerabilities emerge daily. Your assessment and management processes must be continuous. Schedule regular, recurring scans (daily, weekly, monthly, quarterly, depending on asset criticality). Establish clear service level agreements (SLAs) for different severity levels of vulnerabilities to ensure timely remediation.
- Foster Cross-Functional Collaboration: Cybersecurity is a team sport. Break down silos between security, IT operations, development, and business units. Establish regular sync-ups, shared goals, and transparent reporting. Educate teams on their role in the vulnerability management lifecycle.
- Measure, Monitor, and Adapt: Track key metrics like MTTD, MTTR, patch compliance rates, and the overall reduction in critical vulnerabilities. Use this data to identify trends, pinpoint bottlenecks, and continuously refine your processes. Security isn't static; your program shouldn't be either. Regularly review your policies and procedures to adapt to new threats and technological changes.
Your Next Steps: Taking Control of Your Digital Security
Vulnerability Assessment & Management isn't just a technical exercise; it's a strategic imperative for modern organizations. It's about proactive defense, continuous improvement, and building a resilient digital foundation.
If you're just starting, begin by:
- Gaining Asset Visibility: You can't protect what you don't know you have. Inventory all your digital assets.
- Implementing Regular Scans: Start with automated vulnerability scanning on your most critical assets.
- Establishing a Prioritization Framework: Decide how you'll determine which vulnerabilities get attention first.
- Fostering Communication: Ensure your security and IT operations teams are working in lockstep.
The digital landscape will continue to evolve, bringing new technologies and new threats. By embedding robust vulnerability assessment and management into the very fabric of your organization, you're not just reacting to threats; you're building a fortress of continuous vigilance, ready to find and fix those security gaps long before they can be exploited. Take charge of your organization's digital security posture today – the stakes have never been higher.